Posts by Adna Technologies Marketing Team
How to add a new Administrator account to your WordPress website
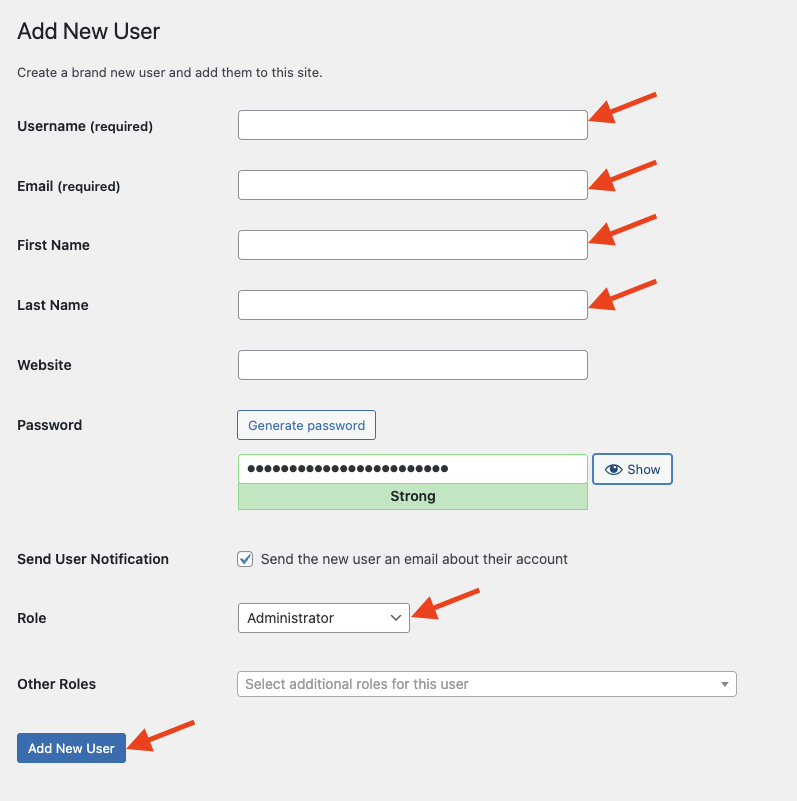
To add a new WordPress administrator to your self-hosted site, follow the steps below. Log in to your WordPress website When you’re logged in, you will be in your Dashboard. Go to Users In the left-side menu, click on Users. Once on the Users menu, click on Add New User At the top of the page, click on Add New User.…
Read MoreMemory and How It Affects The Performance of Your Computer
What is RAM and How Does It Work? RAM (Random Access Memory), often referred to as Memory, is a type of computer memory that stores data your computer needs to access quickly. Think of it like a workspace where your computer can temporarily store information while performing tasks, such as running programs or opening files.…
Read MoreUnderstanding the Limitations of Syncing Files from SharePoint: Challenges and Best Practices
In today’s digital age, businesses rely heavily on cloud platforms like SharePoint to store, share, and collaborate on vast amounts of data. However, as with any system, there are limitations—especially when dealing with extremely large quantities of files. If your organization is attempting to sync 300,000 files or more from SharePoint, it’s essential to be…
Read MoreMicrosoft 365 and the New Commerce Experience
Microsoft’s Office 365 suite has evolved into a powerhouse subscription, allowing many businesses to retire their servers and run entirely from this bundle of cloud-based products. The productivity suite was originally launched a decade ago and now has more than 300 million paid commercial seats and recently, Microsoft is announcing a price increase for many…
Read MoreWhat is a Zero-Day Vulnerability?
What It Is A zero-day vulnerability (also know as zero-day flaw, zero-day exploit) is at its core, a flaw. It is an exploit in the wild that was previously undiscovered, which exposes a vulnerability in software or hardware. A zero-day vulnerability will often create complicated problems well before anyone realizes there is an issue –…
Read MoreEthics and Unauthorized Practice of Law: Preventing Data Breaches in the COVID Era
Reprinted with permission from Buhl, Little, Lynwood & Harris, PLC. Original article can be found at https://bllhlaw.com/preventing-data-breaches-in-the-covid-era/ Every day brings new stories of companies or governments being hacked and private data being leaked. In the first three quarters of 2020 alone, there were 2,935 publicly disclosed breaches, amounting to the disclosure of 36 billion records.1…
Read More5 Ways SMBs Can Save Money on Security
5 Ways SMBs Can Save Money on Security Small-to-medium sized businesses and large enterprises may seem worlds apart, but they face many of the same cyber-security threats. In fact, in recent years, cyber-criminals have increasingly targeted SMBs. This is because it’s widely known that SMBs have a smaller budget, and less in-house expertise, to devote…
Read MoreFour Key Components of a Robust Security Plan Every SMB Must Know
Four Key Components of a Robust Security Plan Every SMB Must Know Most businesses are now technology dependent. This means security concerns aren’t just worrisome to large corporate enterprises anymore, but also the neighborhood sandwich shop, the main street tax advisor, and the local non-profit. Regardless of size or type, practically any organization has valuable…
Read MoreJust Because You’re Not a Big Target, Doesn’t Mean You’re Safe
Just Because You’re Not a Big Target, Doesn’t Mean You’re Safe Not too long ago, the New York Times’ website experienced a well-publicized attack, which raises the question – how can this happen to such a world-renowned corporation? If this can happen to the New York Times, what does this bode for the security of…
Read MoreStay Secure My Friend More Hackers Targeting SMBs
Stay Secure My Friend… More Hackers Targeting SMBs Many SMBs don’t realize it, but the path to some grand cybercrime score of a lifetime may go right through their backdoor. SMBs are commonly vendors, suppliers, or service providers who work with much larger enterprises. Unfortunately, they may be unaware that this makes them a prime…
Read More